
Ethereum’s co-founder, Vitalik Buterin, has released a comprehensive analysis that delves deep into the intricate world of Layer 2 (L2) solutions on the blockchain.
Different types of layer 2shttps://t.co/ry4VTtWhJ1
— vitalik.eth (@VitalikButerin) October 31, 2023
In a chain analysis report published on October 31, Buterin acknowledged the rapid growth of the L2 ecosystem, specifically highlighting the segments of ZK-EVM (Zero-Knowledge Ethereum Virtual Machine) rollups implemented in top projects.
These projects include Arbitrum, StarkNet, Optimism, Scroll, Taiko, and Kakarot.
He commended the enhanced security measures in place and identified L2beat as a reliable source for summarizing the state of each project.
A notable observation of Buterin’s report is the growing diversity within various L2 scaling solutions due to three major factors – the drive of L1, centralized projects, and non-financial applications.
However, this is based on the nature and value of activities conducted on-chain, recognizing that not all activities require the same level of security.
Buterin also pointed out that while Ethereum L1 users may be accustomed to the fees associated with transactions, new users wouldn’t, especially when transitioning from a fee-free environment.
Trade-Offs Among Rollups, Validiums, and Disconnected Systems
Ethereum’s co-founder further analyzed different L2 scaling solutions, notably Rollups, Validiums, and Disconnected Systems, based on their security and scalability capabilities.
Through a detailed chart, Buterin addressed how confident users can be when moving their assets from the L1 to these L2 solutions and back to L1. This involves assessing the risk and security associated with these movements.
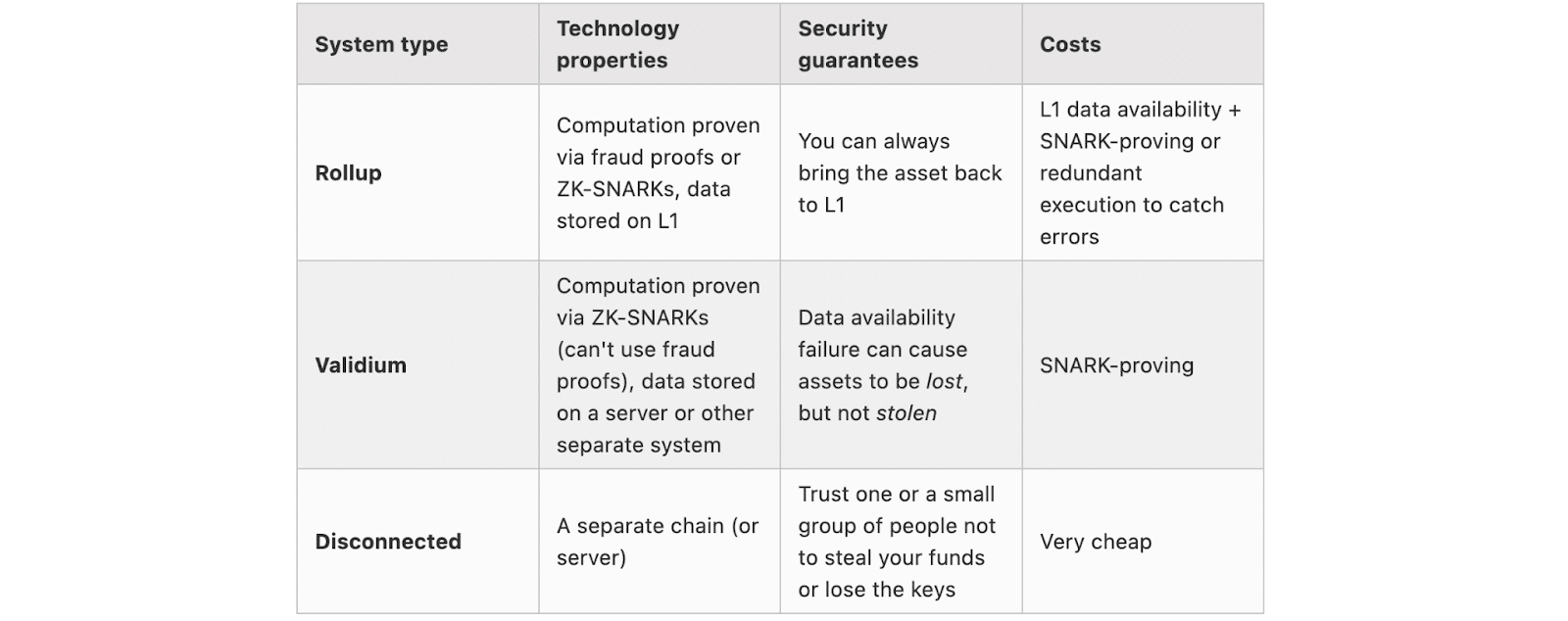
He highlighted solutions such as a validating bridge and explained that the cost of Ethereum’s Native Data Availability versus application needs will be the ultimate feature influencing the choice between different L2 projects.
Buterin noted the importance of a system’s ability to read the Ethereum blockchain in a trustless manner and the security implications associated with this.
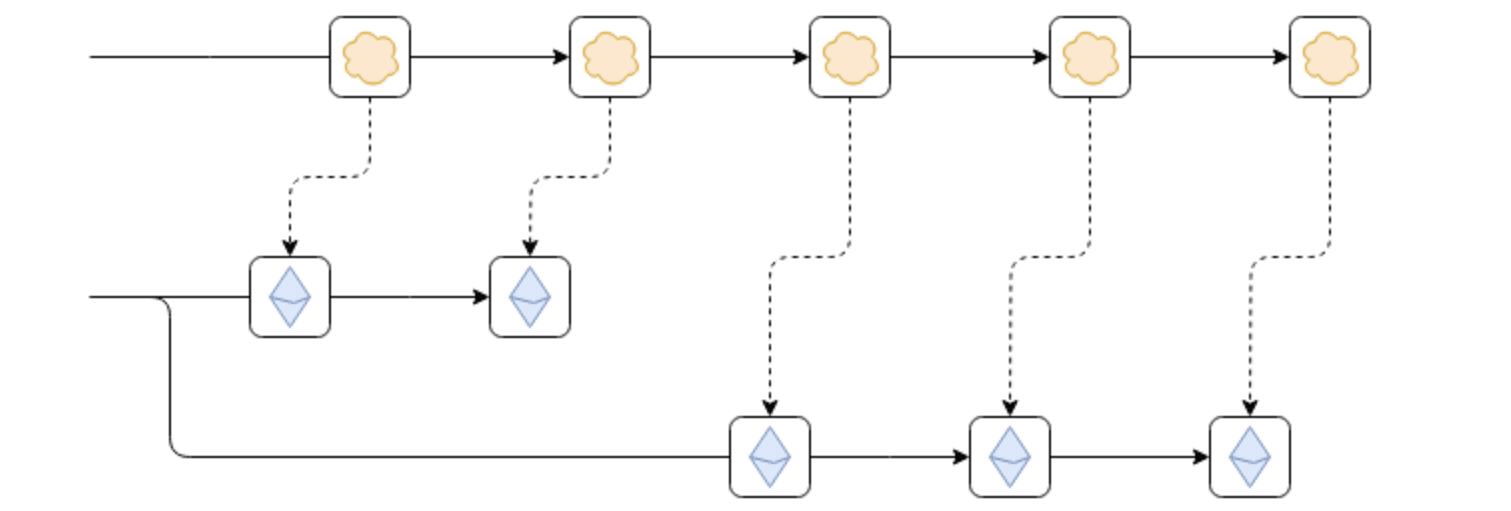
He also proposed two potential solutions to address these concerns – ensuring top chain relies on finalized blocks or enabling top chain to adapt in the event of a blockchain reversion.
The co-founder iterated the concept of transforming a separate chain into a Validium through a two-way validating bridge.
However, he pointed out cases like handling 51% attacks or hard fork upgrades on Ethereum may require more than just technical solutions, possibly involving social commitment.
On a closing note, Buterin explored security aspects of connectedness to Ethereum, particularly regarding withdrawals to Ethereum and data reading.
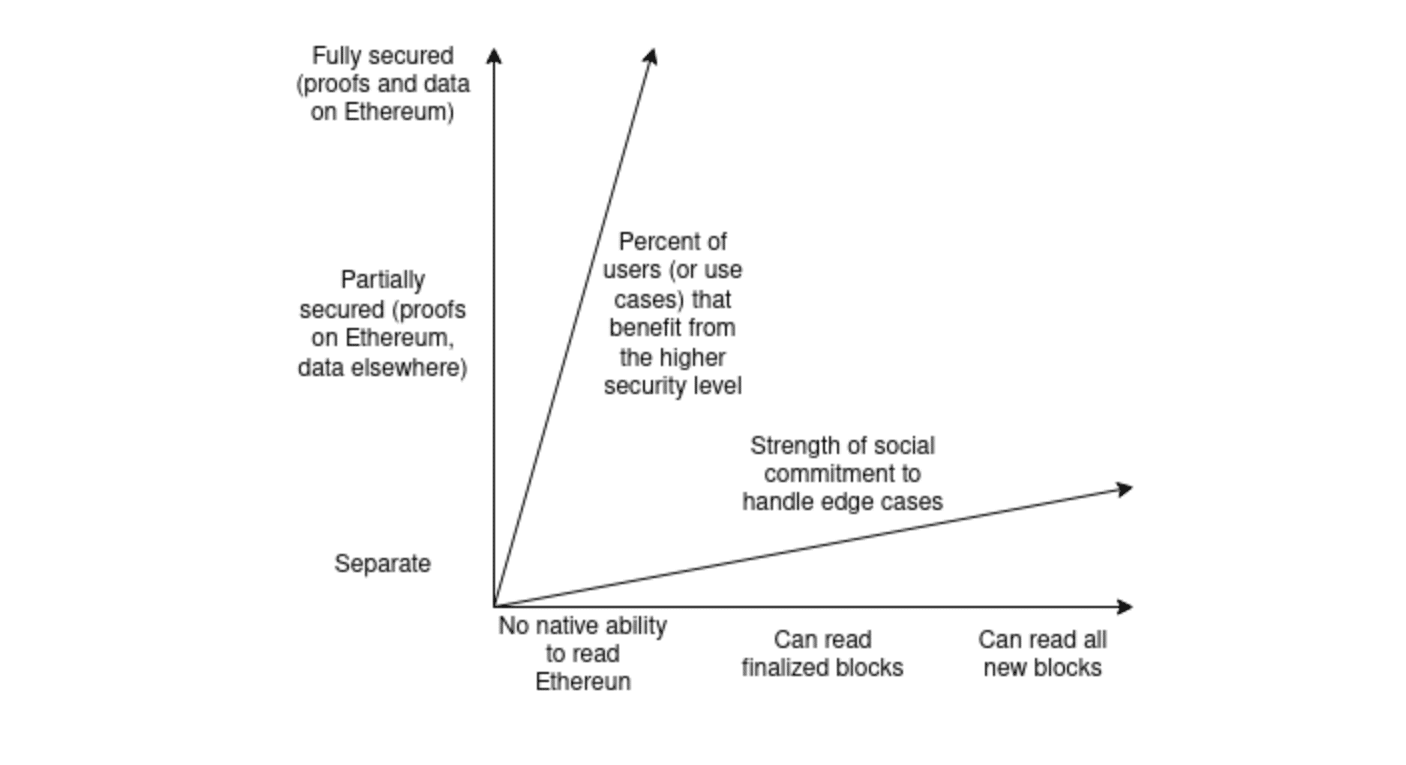
He believes the value of projects deployed across various chains will create a transition pathway with Ethereum as technology evolves.
Buterin’s analytical insight was received by major crypto and ETH enthusiasts on X (formerly Twitter).
The latest article from @VitalikButerin pretty much touches on so many concepts I’ve been highlighting for a while now w.r.t. the subject of classifying Layer 2s and Actualised Ledgers.
Here are a few key points that caught my attention 🧵
1/8 https://t.co/R70zpNH7kR
— 𝙴𝚖𝚖𝚊𝚗𝚞𝚎𝚕 🇬🇭🦉🍕🦄⚡️ (@thepizzaknight_) October 31, 2023
In particular, user ‘@cryptocupid_eth’ pointed out that the key aspects highlighted by Buterin regarding Ethereum’s connectivity align with the contributions of ‘Ethscriptions,’ similar to L2 solutions.
Dear Vitalik,
Greetings! I found your paper incredibly insightful! It brought me some thoughts on how Ethscriptions could connect with the various L2 distinctions you discussed. The focus on security in your piece aligns with Ethscriptions’ core values, striving to foster a… pic.twitter.com/9YukTPsSOx
— 加密丘比特.eth (@cryptocupid_eth) October 31, 2023
However, there were concerns surrounding the use of technology to drive lasting and meaningful adoption of Ethereum.
Another X user ‘@SasuRobert’ argued that popular chains are slow, full of constraints for developers, and have exploits in which users can fail.
First, the best version of any L2 is the one which works as an extension next to L1, making it easy for both users and developers to use that. Thus, bring bridge inside consensus/processing mechanism of the L2, enshrine opcodes to execute cross-chain operations in the name of the… https://t.co/ACgm1aIVbP
— Robert Sasu (@SasuRobert) October 31, 2023
He further suggested the need for better standards and the creation of scalable systems and application-centric L2s to extend the base network.



















